
Restrict Attachment Downloads in OWA Using CA Policy
For IT administrators, securing email communication in the modern workplace extends beyond just inbox monitoring. With the growing adoption of BYOD (Bring Your Own Device) policies, it becomes crucial to control how employees access emails and attachments, particularly when using their personal devices. The risk of data exposure increases significantly when these attachments are accessed via OWA on unmanaged devices.
Unrestricted access to attachments in such scenarios opens vulnerabilities, allowing sensitive documents to be downloaded and shared without authorization, leading to data breaches. To mitigate these risks, administrators must implement OWA mailbox policies that restrict attachment downloads on untrusted devices. In this post, we’ll guide you through configuring Outlook Web App (OWA) mailbox policy and Conditional Access (CA) to prevent unauthorized attachment downloads.
Learn how to tighten data security in Exchange Online by enforcing read-only access and controlling attachment downloads in OWA when accessed from unmanaged devices.
An OWA mailbox policy is a setting within Microsoft Exchange Online that controls what a user can do inside the Outlook Web App. By setting -Conditional parameter to read-only, users can view emails and attachments but can’t download or edit them.
There are two ways to apply these restrictions depending on how broadly or selectively you want to enforce them.
Option A: Update the default policy to Restrict Attachment Downloads in OWA
Before updating the OWA mailbox policy, connect to the Exchange Online PowerShell. To apply download restrictions across the organization using the default OWA policy, execute the below.
|
1 |
Set-OwaMailboxPolicy -Identity OwaMailboxPolicy-Default -ConditionalAccessPolicy ReadOnly |
This enables read-only access when users are on non-compliant or untrusted devices.
Important Note: The key setting here is the ConditionalAccessPolicy on the OwaMailboxPolicy. You can set it to:
- ReadOnly: Users can view emails and attachments but cannot download or edit.
- ReadOnlyPlusAttachmentsBlocked: Blocks both editing and attachment viewing.
- Off: No restrictions.
Option B: Create a custom OWA mailbox policy for targeted users
To avoid unexpected changes across your environment, consider setting up a custom OWA policy. This ensures other users remain unaffected and makes it easier to track who’s subject to restrictions.
Run the following command to create a new OWA mailbox policy.
|
1 2 3 |
New-OwaMailboxPolicy -Name "Restricted Download Access" Set-OwaMailboxPolicy -Identity "Restricted Download Access" -ConditionalAccessPolicy ReadOnly |
This will enforce read-only access for users, meaning they can view emails and attachments but cannot download or edit them.
Now, assign this policy to the targeted users who should be restricted.
|
1 |
Set-CASMailbox -Identity "Rachel" -OwaMailboxPolicy "Restricted Download Access" |
Replace “Rachel” with the username of the user(s) you want to apply this policy to. This step ensures that only the targeted users are affected by the download restrictions.
On the other hand, Conditional Access policy is a rule in Microsoft Entra that checks who the user is, where they are signing in from, and what device they are using. If the user tries to log in from an unmanaged device, the CA policy steps in and applies restrictions. It uses app-enforced restrictions to make apps like OWA limit access such as blocking attachment downloads.
To create a Conditional Access policy, you need Global/Security/Conditional Access administrator permission along with Microsoft Entra ID P1 and P2 licensing options. You can also create CA policies by using pre-defined Conditional Access policy templates.
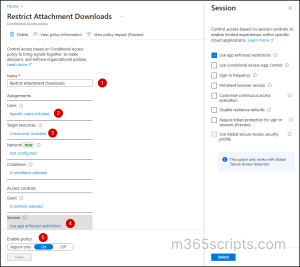
To implement Conditional Access with app-enforced restrictions, follow the steps outlined below.
- Sign into Microsoft Entra admin center.
- Navigate to Identity –> Protection –> Conditional Access.
- Click on Create a new policy.
- Provide a suitable name for your policy.
- In the Assignment section, choose Users. In the Include category, click on Select users and groups and exclude break glass accounts based on requirements.
- Navigate to Target and resources and choose Office 365 Exchange Online under Cloud apps.
- Under Session controls, enable Use app enforced restrictions.
- Confirm your settings and flip the Enable policy toggle from ‘Report-only’ to On.
- Click Create to create your CA policy.
Now, you are all set! With these configurations in place, you ensure that sensitive data stays protected even when accessed from unmanaged or untrusted devices.
After configuring the OWA mailbox and Conditional Access policies, it’s essential to verify whether the settings are functioning as intended.
- Sign in to Outlook on the Web using a test account that is not part of the restricted CA policy.
- Try sending an email with an attachment to the blocked user (Rachel).
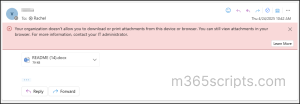
Expected Outcome: Rachel should not be able to download attachments with the following error:
“Your organization doesn’t allow you to download or print attachments from this device or browser. You can still view attachments in your browser. For more information, contact your IT administrator.”
To disable the OWA policy, you can revert it by running the following command.
|
1 |
Remove-OwaMailboxPolicy -Identity "OwaMailboxPolicy-Default" |
Tips:
- Similar to the Outlook Web App, you can also block file downloads in SharePoint and OneDrive using Conditional Access policy.
- In Conditional Access policy, you have the option to block external users from downloading Microsoft 365 files exclusively.
- To keep your mailboxes safe, explore the email security best practices , create role assignment policies and configure only the essential ones for a safe environment.
I hope this blog has provided you with a clear understanding of how to protect email attachments using OWA mailbox policies and Conditional Access. With these settings in place, you can safeguard your organization’s data while maintaining a smooth and secure user experience!
Feel free to reach us through the comments section, if you have any queries.







