How to Manage Apps and Service Principal Objects Using Microsoft Entra PowerShell
Manage Microsoft Entra application registrations and service principals using the Entra PowerShell module after Azure AD deprecation. Create apps, configure permissions, assign owners, and manage service principal settings with cmdlets compatible with existing Azure AD scripts for seamless migration.
If you’re managing apps and service principals in Microsoft 365, there’s one change you can’t afford to overlook: the deprecation of the Azure AD module. Which means the Azure AD cmdlets you previously relied on to register apps, configure permissions, or manage service principals are becoming obsolete. Microsoft Graph PowerShell is now the official replacement, but its different structure makes both daily management tasks and the migration of Azure AD scripts more time-consuming.
To ease this transition, Microsoft now allows you to manage apps using Entra PowerShell. As part of the Microsoft Graph PowerShell SDK, it provides alias for most Azure AD and Graph cmdlets. This allows you to handle app registrations and service principal settings with minimal disruption to your workflow.
In this blog, let’s explore how to manage apps and service principal objects using Microsoft Entra PowerShell.
Before you start managing app registrations and service principals using Microsoft Entra PowerShell, ensure the following prerequisites are in place:
- Microsoft Entra User Account: You’ll need an active Microsoft Azure account. If you don’t have one, you can sign up for a free Azure account.
- Required Roles: Make sure you have either the Application Administrator or Cloud Application Administrator role.
- Check PowerShell Module Status: Confirm that the Microsoft Entra PowerShell module is installed on your system.
Once these prerequisites are met, connect to the Microsoft Entra PowerShell with the following scopes.
Scope: Application.Read.All, Application.ReadWrite.All, AppRoleAssignment.ReadWrite.All, Directory.Read.All
Here are some necessary application and service principal management tasks you can perform using Microsoft Entra PowerShell:
- New Entra app registration
- Create service principal for an app
- Update Entra application properties
- Add owners to the application
- Assign users to service principals
- Get all Azure AD applications
- Delete users from Entra enterprise app
- Find objects created and owned by enterprise apps
- Grant delegate permissions to application
- Revoke delegated permissions from app
- Delete app and service principal in Entra ID
- View deleted apps and service principals
- Restore soft-deleted application objects
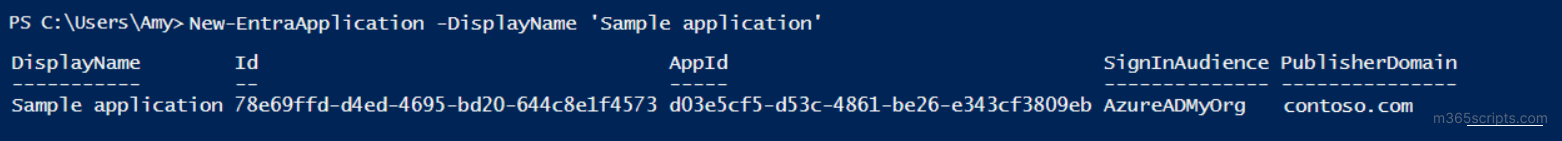
To create a new custom application in Microsoft Entra, you can use the ‘New-EntraApplication’ cmdlet.
|
1 |
New-EntraApplication -DisplayName 'Sample application' |
After running this cmdlet, a new app registration ‘Sample application’ will be successfully created in your Microsoft Entra environment.
The app registration will have two unique IDs: the AppID, which the app uses to sign in, and the ObjectID, which identifies the app in Microsoft Entra.
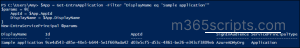
After registering your app, use the ‘New-EntraServicePrincipal’ cmdlet to create its service principal.
|
1 2 3 4 5 6 |
$App = Get-EntraApplication -Filter "DisplayName eq 'Sample application'" $params = @{ AppId = $App.AppId DisplayName = $App.DisplayName } New-EntraServicePrincipal @params |
This cmdlet will add the service principal for an app registration ‘Sample application’ in your Microsoft 365.
Note: Replace ‘Sample application’ with the display name of the app for which you want to create a service principal.
You can use the ‘Set-EntraApplication’ cmdlet to modify the properties of Entra app registrations.
For example, if you want to update your app’s display name, you can use this command like below.
|
1 |
Set-EntraApplication -ApplicationId (Get-EntraApplication -Filter "DisplayName eq 'Sample application'").Id -DisplayName 'My Sample application' |
Similar to this, you can update other properties such as redirect URI and resource access, as shown in the following example.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 |
$application = Get-EntraApplication -Filter "DisplayName eq 'Sample application'" $requiredAccess = New-Object Microsoft.Open.MSGraph.Model.ResourceAccess $requiredAccess.Id = "a154be20-db9c-4678-8ab7-66f6cc099a59" $requiredAccess.Type = "Scope" $DelegatedResourceAccess = New-Object Microsoft.Open.MSGraph.Model.RequiredResourceAccess $DelegatedResourceAccess.ResourceAppId = " (Get-EntraServicePrincipal -Filter "displayName eq 'Microsoft Graph'").AppId " $DelegatedResourceAccess.ResourceAccess = $requiredAccess $RedirectURI = New-Object Microsoft.Open.MSGraph.Model.PublicClientApplication $RedirectURI.RedirectUris = @("http://localhost") Set-EntraApplication -ApplicationId $application.Id -PublicClient $RedirectURI -RequiredResourceAccess $DelegatedResourceAccess |
This PowerShell snippet assigns the User.Read.All permission and sets authentication redirect URI for the ‘Sample application’.
Note: When you assign only new permissions, any existing permissions that haven’t been granted with admin consent will be removed. Updating permissions alone doesn’t grant them consent, you must manually grant admin consent in the Microsoft Entra admin center.
Managing app owners ensures proper access governance and accountability. It helps you gain control over your enterprise applications.
List Owners of the Enterprise Applications
To view the owners of a specific service principal, you can use the ‘Get-EntraServicePrincipalOwner’ cmdlet.
|
1 |
Get-EntraServicePrincipalOwner -ServicePrincipalId (Get-EntraServicePrincipal -Filter "DisplayName eq 'Sample application'").Id -All |
You can also retrieve owners from all service principals, using the following method.
|
1 2 3 4 5 6 7 8 9 10 11 |
Get-EntraServicePrincipal -All | ForEach-Object { $Serviceprincipal = $_ Get-EntraServicePrincipalOwner -ServicePrincipalId $Serviceprincipal.Id -All | ForEach-Object { [PSCustomObject]@{ 'Service Principal Name' = $Serviceprincipal.DisplayName 'Owner Name' = $_.DisplayName 'Owner ID' = $_.Id 'Owner Type' = $_.'@odata.type' } } } | Format-Table -AutoSize |
Running this command will display all the Enterprise apps and their owners in your organization, simplifying app administration.
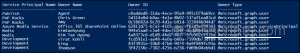
Assign Owner to the Enterprise Application
If you want to assign an owner to a service principal, you can use the following cmdlet.
|
1 |
Add-EntraServicePrincipalOwner -ServicePrincipalId (Get-EntraServicePrincipal -Filter "DisplayName eq 'Sample application'").Id -OwnerId (Get-EntraUser -UserId '[email protected]').Id |
This cmdlet assigns ‘[email protected]’ as the owner of service principal ‘Sample application’.
To assign user to the service principal, you can use the following cmdlet.
|
1 2 3 |
$ServicePrincipalObject = Get-EntraServicePrincipal -Filter "DisplayName eq 'Sample application'" New-EntraServicePrincipalAppRoleAssignment -ServicePrincipalId $ServicePrincipalObject.Id -ResourceId $ServicePrincipalObject.Id -Id "$([Guid]::Empty)" -PrincipalId (Get-EntraUser -UserId '[email protected]').Id |
This cmdlet adds ‘[email protected]’ to the ‘Sample application’ service principal.
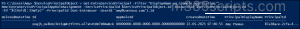
Additionally, you can also assign a group to the service principal using Microsoft Entra PowerShell.
|
1 2 3 |
$ServicePrincipalObject = Get-EntraServicePrincipal -Filter "DisplayName eq 'Sample application'" New-EntraServicePrincipalAppRoleAssignment -ServicePrincipalId $ServicePrincipalObject.Id -ResourceId $ServicePrincipalObject.Id -Id "$([Guid]::Empty)" -PrincipalId (Get-EntraGroup -Filter “DisplayName eq 'All Company'”).Id |
Here, the group ‘All Company’ is assigned to the ‘Sample application’ service principal.
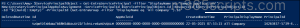
You can export all user and group assignments to the service principals using the following Entra PowerShell cmdlet.
This is particularly useful for app owners or security teams to regularly review assigned users, reducing the risk of unintended access sprawl.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 |
$results = Get-EntraServicePrincipal -All | ForEach-Object { $sp = $_ $assignments = Get-EntraServicePrincipalAppRoleAssignedTo -ServicePrincipalId $sp.Id $userIds = $assignments | Where-Object { $_.PrincipalType -eq 'User' } | Select-Object -ExpandProperty PrincipalId $groupIds = $assignments | Where-Object { $_.PrincipalType -eq 'Group' } | Select-Object -ExpandProperty PrincipalId $userNames = if ($userIds) { $userIds | ForEach-Object { (Get-EntraUser -UserId $_).DisplayName } } else { @() } $groupNames = if ($groupIds) { $groupIds | ForEach-Object { (Get-EntraGroup -GroupId $_).DisplayName } } else { @() } if ($userNames.Count -gt 0 -or $groupNames.Count -gt 0) { [PSCustomObject]@{ ServicePrincipalName = $sp.DisplayName Users = ($userNames -join ", ") Groups = ($groupNames -join ", ") } } } $results | Export-Csv -Path "./ServicePrincipalAssignments.csv" -NoTypeInformation |
Once the PS snippet is executed, it generates a CSV file containing all service principals along with their assigned users and groups.
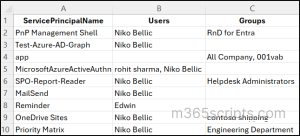
If you want to remove user access to the application, use the following PowerShell command.
|
1 |
Get-EntraServicePrincipalAppRoleAssignedTo -ServicePrincipalId (Get-EntraServicePrincipal -Filter "DisplayName eq 'Sample application'").Id | ForEach-Object {Remove-EntraServicePrincipalAppRoleAssignment -ServicePrincipalId $_.ResourceId -AppRoleAssignmentId $_.Id} |
This command will remove all user and group assignments from ‘Sample application’ service principal.
To list all objects that were created or owned by a specific service principal, run the following cmdlets.
View Objects Created by Service Principal:
|
1 |
Get-EntraServicePrincipalCreatedObject -ServicePrincipalId (Get-EntraServicePrincipal -Filter "DisplayName eq 'Sample application'").Id | Select Id, DisplayName | ft |
This cmdlet will display list of all objects that are created by the ‘Sample application’.
View Objects Owned by Service Principal:
|
1 |
Get-EntraServicePrincipalOwnedObject -ServicePrincipalId (Get-EntraServicePrincipal -Filter "DisplayName eq 'Sample application'").Id | Select Id, DisplayName | ft |
This cmdlet will return all object that are owned by the ‘Sample application’.
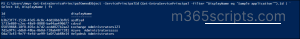
You can grant permissions to your app registrations using ‘New-EntraOauth2PermissionGrant’ Entra PowerShell cmdlet. To delegate permissions for service principal, you need the following information.
- ClientId: Object ID of your service principal.
- ConsentType: AllPrincipals (for all users) or Principal (for a specific user).
- ResourceId: Object ID of the service principal (resource app) that contains required permission.
- Scope: Permissions you want to delegate to your service principal.
|
1 2 3 4 |
$ClientServicePrincipalId = (Get-EntraServicePrincipal -Filter "DisplayName eq 'Sample application'").Id $ResourceServicePrincipalId = (Get-EntraServicePrincipal -Filter "DisplayName eq 'Microsoft Graph'").Id New-EntraOauth2PermissionGrant -ClientId $ClientServicePrincipalId -ConsentType 'AllPrincipals' -ResourceId $ResourceServicePrincipalId -Scope 'User.Read.All Group.Read.All' |
This cmdlet grants the delegated permissions for ‘Sample application’ to access all users’ profile and group details across the organization. It allows signed-in users of the app to retrieve data without requiring individual consent.
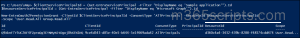
For comprehensive security, regularly review the enterprise application permissions to quickly identify and remove any unintended access or excessive delegated scopes.
To remove delegated permissions granted to service principal, use the following cmdlet.
|
1 |
Get-EntraOAuth2PermissionGrant | Where-Object {$_.ClientId -eq (Get-EntraServicePrincipal -Filter "DisplayName eq 'Sample application'").Id} | Remove-EntraOauth2PermissionGrant |
Here, this command revokes the delegated permissions from ‘Sample application’ service principal. Similarly, you can manage application permissions as well to ensure your enterprise apps follow least privilege access and maintain security compliance.
To remove application or service principal from Microsoft Entra ID, use the ‘Remove-EntraApplication’ and ‘Remove-EntraServicePrincipal’ cmdlets.
|
1 2 3 4 5 |
#Delete an app registration Get-EntraApplication -Filter "DisplayName eq 'Sample application'" | Remove-EntraApplication #Delete a service principal Get-EntraServicePrincipal -Filter "DisplayName eq 'Sample application'" | Remove-EntraServicePrincipal |
Run the commands respectively to remove apps and service principals in Microsoft Entra ID. Replace the ‘Sample application’ with display name of the app or service principal you want to delete.
Tip: Follow the best practices to remove unused applications to protect your applications against token theft attacks.
When you delete an application or service principal in Microsoft 365, it is moved to a soft-deleted state. Here, the object remains suspended for 30-days. After this period, it will be permanently deleted.
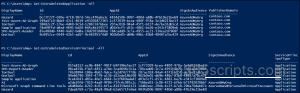
To find applications and service principals in the soft-deleted state, use the following Entra PowerShell cmdlets.
|
1 2 3 4 5 |
#List all deleted app registrations Get-EntraDeletedApplication –All #List all deleted service principals Get-EntraDeletedServicePrincipal -All |
To restore soft-deleted app registrations and enterprise applications, you can use the following cmdlet.
|
1 2 3 4 5 |
#Restore an application from soft-delete state Get-EntraDeletedApplication -Filter "DisplayName eq 'Sample application'" | Restore-EntraDeletedDirectoryObject #Restore a service principal from soft-delete state Get-EntraDeletedServicePrincipal -Filter "DisplayName eq 'Sample application'" | Restore-EntraDeletedDirectoryObject |
These cmdlets will restore the ‘Sample application’ and its service principal from the soft-deleted state. When an app or service principal is restored, all of its properties are recovered as well.
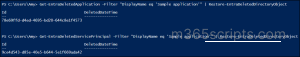
Note: If you try to restore a soft-deleted service principal without restoring its associated app registration, it will result in the following error. To avoid this, make sure to restore the app registration before attempting to restore the service principal.
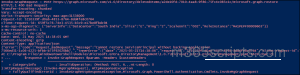
You can also bulk restore application registrations and service principals in PowerShell by using a CSV file that contains the Application ID and ServicePrincipal/Object ID for each entry.
I hope this blog gave you valuable insights to manage apps using Entra PowerShell. If you have any questions or need further guidance, feel free to reach out in the comments section.