Manage Authentication Methods for A User Using PowerShell
Manage Microsoft Entra ID user authentication methods using Microsoft Graph PowerShell for efficient MFA administration. View registered methods, reset authenticator apps, remove phone numbers, and update security configurations at scale. Handle MFA lockouts and ensure compliance across your Microsoft 365 environment.
Imagine a user suddenly locked out because they lost their phone, or needing urgent MFA resets in the middle of a workday. If you’re a Microsoft 365 admin, these scenarios are all too familiar. With Microsoft mandating MFA for all users, administrators must ensure that users can authenticate reliably, while also securing accounts from MFA registration attacks. This involves monitoring registered authentication methods, updating or resetting them when needed, and ensuring compliance.
Manually managing authentication methods for a handful of users may be feasible, but in larger environments, doing this efficiently becomes a challenge. That’s where Microsoft Graph PowerShell comes in. This blog post will walk you through how to manage user authentication methods in Entra ID using Microsoft Graph PowerShell.
Microsoft 365 supports multiple authentication methods, which can be used as primary or secondary factors during sign-ins. Some methods, like passwords and FIDO2 keys, serve as primary authentication, while others are secondary, used with MFA or self-service password reset (SSPR).
The following table summarizes when each authentication method can be used:
| Microsoft 365 Authentication Methods | Primary Authentication | Secondary Authentication |
| Windows Hello for Business | Yes | MFA |
| Microsoft Authenticator push | No | MFA and SSPR |
| Microsoft Authenticator passwordless | Yes | No |
| Microsoft Authenticator passkey | Yes | MFA |
| Authenticator Lite | No | MFA |
| Passkey (FIDO2) | Yes | MFA |
| Certificate-based authentication (CBA) | Yes | MFA |
| Hardware OATH tokens (preview) | No | MFA and SSPR |
| Software OATH tokens | No | MFA and SSPR |
| External authentication methods (preview) | No | MFA |
| Temporary Access Pass (TAP) | Yes | MFA |
| Text | Yes | MFA and SSPR |
| Voice call | No | MFA and SSPR |
| QR code | Yes | No |
| Password | Yes | No |
Now, let’s explore how to manage a user’s authentication methods using Microsoft Graph PowerShell.
Before you start, connect to Microsoft Graph PowerShell module with the UserAuthenticationMethod.ReadWrite.All scope. Use an account in Microsoft Entra that’s assigned either the Privileged Authentication Administrator or Authentication Administrator role.
Once connected with the correct roles and permissions, Authentication administrators can:
- Get User’s Authentication Methods in Microsoft 365
- Manage Phone Authentication Methods in Microsoft 365
- Manage Email Authentication Methods in Microsoft 365
- Manage FIDO2 Security Keys for a User in Microsoft 365
- Manage Microsoft Authenticator App Methods
- Manage Software OATH Tokens in Entra ID
- Manage Temporary Access Pass in Microsoft 365
- Reset a User’s Password in Microsoft 365
- Reset MFA for User in Microsoft 365
Find the globally unique identifiers for Microsoft Authentication methods:
|
Microsoft 365 Authentication Methods |
Globally Unique ID of the Authentication Method |
| Mobile phone type | 3179e48a-750b-4051-897c-87b9720928f7 |
| Office phone type | e37fc753-ff3b-4958-9484-eaa9425c82bc |
| AlternateMobile phone type | b6332ec1-7057-4abe-9331-3d72feddfe41 |
| 3ddfcfc8-9383-446f-83cc-3ab9be4be18f | |
| Microsoft Authenticator App | 397c2b28-dac5-4b1e-b306-5d88c4ec2b36 |
| Temporary Access Pass (TAP) | 36b37365-d471-4039-b376-c8e1114db0d3 |
| Password | 28c10230-6103-485e-b985-444c60001490 |
| Hardware OATH | 3dee0e53-f50f-43ef-85c0-b44689f2d66d
|
| FIDO2 |
Fido2 |
Administrators should check a user’s registered authentication methods to manage MFA and protect against threats like MFA fatigue and SIM swapping attacks. Run the below to get a user’s registered authentication methods in the organization.
|
1 |
Get-MgUserAuthenticationMethod -UserId <userId> |
Replace <userId> with the user’s unique ID or email address to specify the account you want to review.
The output displays all the globally unique IDs of the authentication methods registered for that user.
As organizations increasingly adopt to configure MFA, it becomes essential for administrators to monitor the authentication methods registered by all users. To do so, you can export registered authentication methods in Microsoft 365 using a dedicated PowerShell script, which allows filtering for admins and licensed users.
- List a user’s phone authentication methods
- Add a phone number for a user
- Remove a user’s phone authentication method
Phone numbers serve as one of the most widely used methods for Multi-Factor Authentication (MFA) and account recovery in Microsoft 365. Administrators can add, monitor, or remove phone numbers to strengthen account security and ensure only valid devices are used for authentication.
✅ List a User’s Phone Authentication Methods
Use the command below to list all phone authentication methods registered for the user.
|
1 |
Get-MgUserAuthenticationPhoneMethod -UserId <userId> |
Replace <userId> with the user’s unique ID or email address to specify the account.
This command retrieves all phone authentication IDs a user has registered for MFA. It helps administrators audit user authentication setups, detect outdated or unauthorized numbers, and ensure compliance with security policies.
✅ Create a Mobile Authentication Method for a Specific User
To add a new phone number for a user, use the following command.
|
1 2 3 4 5 |
$params = @{ "phoneNumber" = "+1 2065555555" "phoneType" = "mobile" } New-MgUserAuthenticationPhoneMethod -UserId <userId> -BodyParameter $params |
Update the <userId> with the user’s ID or email, phoneNumber with their number, and phoneType as ‘mobile’ for SMS/calls/app or ‘office’ for voice only.
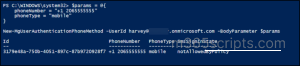
When a user is locked out or cannot access their primary authentication method, a mobile phone can provide temporary MFA. This method is convenient but less secure, so it’s best used as a short-term solution.
✅ Remove a User’s Phone Authentication Method
Implementing strong authentication methods are essential to protect your organization’s data and defend against potential. If weaker authentication methods are detected, IT teams can promptly remove less secure phone-based MFA options, ensuring accounts remain protected. Run the command below to delete a phone authentication method of a user.
|
1 |
Remove-MgUserAuthenticationPhoneMethod -UserId <userId> - PhoneAuthenticationMethodId <phoneMethodId> |
Replace <userId> with the user’s unique ID or email address, and <phoneMethodId> with the ID of the phone method you want to remove.
This command removes a specified phone number from the user’s MFA methods. After removal, the phone can no longer be used for authentication, reducing the risk of lost or compromised devices.
Manually deleting phone authentication for bulk users is a drag. Save time and effort with the dedicated PowerShell script that handles the entire cleanup in one go!
Email addresses are commonly used for account recovery and MFA. They allow users to reset passwords, verify identity, and receive security notifications.
- List a user’s email authentication method
- Update a user’s email authentication method
- Remove a user’s email authentication method
- Bulk Removal of users’ email authentication method
✅List a User’s Email Authentication Method
Run the following to check all emails the user has linked for MFA or account recovery purposes.
|
1 |
Get-MgUserAuthenticationEmailMethod -UserId <userId> |
Replace <userId> with the user’s unique ID or email address. This helps admins review recovery options and ensure only authorized emails are associated with the account.
✅Update a User’s Email Authentication Method
When a user experiences a security threat like a compromised email account, update their registered email to protect MFA and account recovery.
|
1 2 3 4 |
$body = @{ "emailAddress" = "<emailID>" } Update-MgUserAuthenticationEmailMethod -UserId <userId> -EmailAuthenticationMethodId <emailMethodId> -BodyParameter $body |
Here,
- Replace <userId> with the user’s unique ID or email address.
- Replace <emailMethodId> with the ID of the email authentication method you want to update.
- In the $body section, replace “<emailID>” with the new email address to be registered.

This ensures that the user’s MFA notifications and account recovery options are updated and remain secure.
✅ Remove a User’s Email Authentication Method
Use the following command to delete a registered email address.
|
1 |
Remove-MgUserAuthenticationEmailMethod -UserId <userId> - EmailAuthenticationMethodId <emailMethodId> |
Replace <userId> with the user’s unique ID or email address, and <emailMethodId> with the globally unique ID of the email method to remove. This removes an obsolete or compromised email, helping prevent unauthorized access.
✅Bulk Removing Email Authentication Methods for Microsoft 365 Users
Removing email authentication methods in bulk becomes essential when dealing with a large number of users. This is particularly useful during transitions, such as migrating to stronger authentication methods, onboarding or offboarding employees, or responding to security threats like phishing attacks.
Use this PowerShell script to remove email authentication methods for multiple users at once. Provide the UserId for each user in a CSV file as input.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 |
# Import the CSV file containing only UserIds $userList = Import-Csv -Path "<InputFilePath>" # Define output path $outputPath = "<OutputFilePath>" $emailMethodId = "3ddfcfc8-9383-446f-83cc-3ab9be4be18f" $results = @() foreach ($entry in $userList) { $userId = $entry.UserId try { Remove-MgUserAuthenticationEmailMethod -UserId $userId -EmailAuthenticationMethodId $emailMethodId -ErrorAction Stop $message = "Successfully removed email method: $emailMethodId for user: $userId" $results += [PSCustomObject]@{ Message = $message } } catch { $message = "Failed to remove email method: $emailMethodId for user: $userId. Error: $_" $results += [PSCustomObject]@{ Message = $message } } } # Export results to CSV $results | Export-Csv -Path $outputPath -NoTypeInformation Write-Host "Results exported to $outputPath" |
Input CSV file:
Executing this script creates a log file that confirms the removal of email authentication methods for multiple users in Microsoft 365.
FIDO2 security keys provide strong password-less authentication, replacing traditional passwords with hardware or biometric devices. Administrators can view and remove registered keys to maintain tight control over authorized access devices.
✅ List a User’s FIDO2 Security Keys
You can retrieve all FIDO2 keys registered by a user using the following PowerShell command:
|
1 |
Get-MgUserAuthenticationFido2Method -UserId <userId> |
Replace <userId> with the user’s unique ID or email address. The above command retrieves all FIDO2 keys registered by the specified user, helping you monitor device access.
✅ Remove a User’s FIDO2 Security Key
To delete a specific FIDO2 key using MS Graph PowerShell, run the following command.
|
1 |
Remove-MgUserAuthenticationFido2Method -UserId <userId> - Fido2AuthenticationMethodId <fido2KeyId> |
This command removes the selected key from the user’s authentication methods. Replace <userId> with the user’s unique ID or email address, and <fido2KeyId> with the ID of the FIDO2 key.
Authenticator apps provide time-based one-time passcodes (TOTP) for MFA, offering strong protection against account compromise. Administrators can monitor and manage authenticator app registrations to maintain security compliance.
✅ List a User’s Authenticator App Registrations
Run the following to retrieve all registered Microsoft Authenticator instances for a user.
|
1 |
Get-MgUserAuthenticationMicrosoftAuthenticatorMethod -UserId <userId> |
Replace <userId> with the user’s unique ID or email address. Executing the above allows administrators to ensure that only approved devices are used for MFA and detect anomalies.
✅ Remove a User’s Authenticator App Registration
Use the following command to delete a user’s registered authenticator app method.
|
1 |
Remove-MgUserAuthenticationMicrosoftAuthenticatorMethod -UserId <userId> -MicrosoftAuthenticatorAuthenticationMethodId <authAppId> |
Replace <userId> with the user’s unique ID or email address, and <authAppId> with the ID of the authenticator app method you want to remove. This action helps prevent unauthorized access by disabling authentication from devices that are lost, stolen, or no longer in use.
Software OATH tokens are used to generate time-based, one-time passcodes that enhance security as part of multi-factor authentication (MFA). Within Microsoft 365, administrators can easily track and manage these tokens to ensure that only trusted methods are available for user authentication.
✅ List a User’s OATH Tokens in Entra ID
Check which software or hardware OATH tokens a user has registered for MFA.
|
1 |
Get-MgUserAuthenticationSoftwareOathMethod -UserId <userId> |
Replace <userId> with the user’s unique ID or email address. This helps administrators monitor active tokens and ensure only authorized methods are in use.
✅ Remove a User’s OATH Token
Delete a specific OATH token to prevent it from being used for authentication.
|
1 |
Remove-MgUserAuthenticationSoftwareOathMethod -UserId <userId> - SoftwareOathAuthenticationMethodId <oathId> |
Replace <userId> with the user’s unique ID or email address, and <oathId> with the ID of the token you want to remove. This action helps maintain account security by disabling compromised or unnecessary tokens.
Temporary Access Passes allow users to sign in without a password for a limited time. Its primary purpose is to enable onboarding of new passwordless authentication methods or to help users regain access to their accounts securely. Administrators can create, monitor, and revoke TAPs, ensuring temporary access is granted only when needed and removed promptly afterward.
✅ List a User’s TAPs in Microsoft 365
Retrieve all active Temporary Access Passes for short-term authentication access.
|
1 |
Get-MgUserAuthenticationTemporaryAccessPassMethod -UserId <userId> |
Replace <userId> with the user’s unique ID or email address. This helps administrators view existing TAPs and manage temporary access permissions.
✅ Create a Temporary Access Pass in Entra ID
You can generate a TAP that allows a user to sign in without a password for a set period. You can control whether the pass can be used once or multiple times and how long it will remain active.
|
1 2 3 4 5 |
$params = @{ "isUsableOnce" = $true "lifetimeInMinutes" = 60 } New-MgUserAuthenticationTemporaryAccessPassMethod -UserId <userId> -BodyParameter $params |
Replace <userId> with the user’s unique ID or email address. Adjust the parameters to define how long the TAP is valid and whether it can be used once or multiple times.
✅ Remove a User’s TAP in Microsoft Entra
Even if a TAP has an expiration time, it is safer to revoke it immediately if it is no longer needed or if it might have been compromised. Removing the pass early prevents unauthorized users from taking advantage of it.
|
1 |
Remove-MgUserAuthenticationTemporaryAccessPassMethod -UserId <userId> -TemporaryAccessPassAuthenticationMethodId <tapId> |
Replace <userId> with the user’s unique ID or email address, and <tapId> with the ID of the TAP to be removed. This ensures that unused or compromised passes are disabled immediately.
When users forget their password or when a security event requires an immediate password change, you can reset the user’s password using PowerShell.
|
1 |
Update-MgUser -UserId <userid> -PasswordProfile @{forceChangePasswordNextSignIn = $true; password = "<newpassword>"} |
Replace <userId> with the user’s unique ID or email address, and <newpassword> with the desired temporary password.
Executing this command will reset the user’s password to the specified value and require them to change it upon their next sign-in.
To prompt a user to re-register for multi-factor authentication (MFA), you can invalidate their existing authentication methods that enforce re-registration. Use the following cmdlet to revoke the user’s active sign-in sessions.
|
1 |
Revoke-MgUserSignInSession -UserId <userid> |
Replace <userId> with the user’s unique ID or email address. This forces the user to sign in again, and they will be required to re-register for MFA during the next sign-in attempt.
For scenarios where you need to reset Multi-Factor Authentication for bulk users at once, you can use a dedicated PowerShell script with an input CSV file. The script also allows you to remove specific authentication methods such as Microsoft Authenticator, Software OATH tokens, and more, helping you manage MFA settings efficiently across your organization.
I hope this blog has helped you understand how to effectively manage user authentication methods in Microsoft 365 using Microsoft Graph PowerShell. Moving away from the legacy admin experience to PowerShell not only streamlines authentication management but also strengthens your overall security posture. Feel free to reach us through the comment section if you have any questions.