
How to Manage External Access in Microsoft Teams for Secure Collaboration
Configure Microsoft Teams external access settings to control communication with users outside your organization. Manage organization-wide external domains, create user-specific external access policies, and balance collaboration capabilities with security requirements to prevent unauthorized interactions.
By default, Microsoft Teams allows communication with all external users through calls, chats, and meetings. While this fosters seamless collaboration with external users, it also poses risks like unauthorized interactions, brand impersonation in Microsoft Teams, and more. Effective management of external access in Microsoft Teams is crucial to strike the right balance between collaboration and security. In this blog, we will explore the external access settings in Microsoft Teams, discuss a recent update to external access policies, and explain how it enhances Microsoft Teams security.
Monitoring Teams with external user access is essential to ensure organizational security and compliance. This allows administrators to review and tighten guest access permissions. Managing collaboration with external users requires understanding two levels of control: organization settings and user policies. For a user to collaborate externally, both the organization settings and the individual user’s policy must allow it. If either is disabled, the user cannot access external features. To configure external access in Teams, admins must first set up the organization-wide settings to define the types of external interactions allowed. Then, they can apply targeted external access policies to ensure only authorized users are enabled.
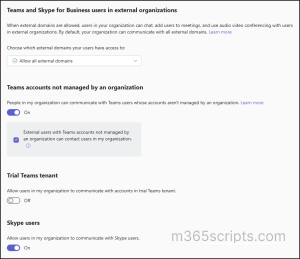
Admins can manage organization-level external access settings using either the Teams admin center or PowerShell. Since these settings mainly involve simple toggles, many admins prefer to configure them via the Teams admin center. To access these settings, navigate to Microsoft Teams admin center → Users → External access.
- Choose which external domains your users have access to – Since all external domains are allowed by default, admins should fine-tune the settings to allow or block specific domains based on the organization’s needs. The four options available for managing external domains are:
-
- Allow all external domains: The default setting that enables communication with any external Teams or Skype for Business domain, as long as external access is enabled on their side.
- Allow only specific external domains: This option allows communication to a list of allowed domains, blocking all others. (For secure external access to Microsoft Teams, you can choose this option.)
- Block only specific domains: You can block certain domains while still allowing communication with all others.
- Block all external domains: If your organization don’t have the need to collaborate with external users, then disable external access in Microsoft Teams using this option.
By default, blocking a domain does not automatically block its subdomains. To block all subdomains in Teams, you can use the PowerShell cmdlet ‘Set-CsTenantFederationConfiguration’ with the -BlockAllSubdomains parameter.
You can also restrict guest access to specific Microsoft 365 groups instead of blocking external access globally using sensitivity labels and PowerShell, giving you more granular control over teams and data.
- Control chats and meetings with external users not managed by an organization – You can choose if users in your organization can chat or meet with users who have personal Microsoft Teams accounts. If you choose to allow external participants in meetings, make sure the following settings are configured to enforce security:
- Verification checks for joining Teams meetings – Helps block bots from accessing meetings.
- Meeting lobby – Allows you to approve or deny participants before they join the meeting.
- Email verification – Prevents anonymous users from joining meetings without confirming their identity.
- Sensitive content detection during screen sharing – Detects sensitive information shared during meetings and notifies the meeting organizer and presenter to take appropriate action.
- External access with trial-only tenants – You can use this option to manage communication with Teams trial-only tenants (tenants with no purchased license), which is disabled by default.
- Manage external communication with Skype users – With this setting enabled, Teams users can search for and initiate one-on-one conversations or audio/video calls with Skype users, and vice versa.
Note:
External users cannot access internal teams, sites, or Microsoft 365 resources. To assign access to teams, consider adding external users to shared channels or grant them guest access. Additionally, you can onboard external users through an access package to ensure they only receive access to necessary teams for a defined period while maintaining security and compliance.
After setting external access at the organization level, admins can control which users can chat or meet with people outside by applying external access policies. As of now, external access policies for Microsoft Teams users can be configured only using PowerShell. Here’s a breakdown of the parameters available for the ‘CsExternalAccessPolicy’ cmdlet, that can be used to manage Teams external access policies:
| Configuration | Parameter |
| Allow or prevent meetings and chat with other Teams organizations and Skype for Business
|
-EnableFederationAccess |
| Allow or prevent chat with external Teams users not managed by an organization
|
-EnableTeamsConsumerAccess |
| Allow or prevent external users not managed by an organization from initiating a conversation
|
-EnableTeamsConsumerInbound |
| Allow or prevent chat with Skype users
|
-EnablePublicCloudAccess |
To manage external meetings and chats for specific users in Microsoft Teams:
- Turn off the default global policy.
- Create a new policy with the appropriate external access settings.
- Assign the new policy to the users who need it.
For example,
After connecting to Microsoft Teams PowerShell, run the below cmdlets.
|
1 |
Set-CsExternalAccessPolicy -EnableFederationAccess $false |
The cmdlet ‘Set-CsExternalAccessPolicy’ first disables federation access for all users.
|
1 2 3 4 5 |
New-CsExternalAccessPolicy -Identity "CustomPolicy" -EnableFederationAccess $true $users_ids = @("[email protected]", “[email protected]”) New-CsBatchPolicyAssignmentOperation -PolicyType ExternalAccessPolicy -PolicyName "CustomPolicy" -Identity $users_ids |
Then, the ‘New-CsExternalAccessPolicy’ cmdlet is used to create and enable a new policy that allows federation. Finally, the ‘New-CsBatchPolicyAssignmentOperation’ cmdlet applies the policy to Rachel and Harvey, enabling external communications to them.
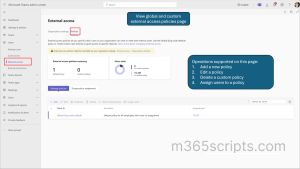
Previously, administrators had to rely on PowerShell commands to manage Microsoft Teams external access policies. Now, Microsoft has introduced a dedicated External Access Policies tab in the Teams admin center (MC938541). This enhancement eliminates the need for PowerShell commands, enabling admins to manage these policies directly through the Teams admin center UI. The rollout timeline for general availability worldwide is from mid-January 2025 to late January 2025. The External Access Policies tab can be found in the Teams admin center under User > External access > Policies tab.
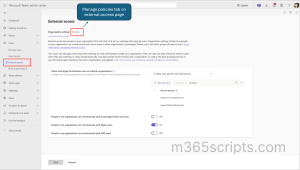
This new feature simplifies the management of these policies by providing a user-friendly interface for:
- Viewing existing external access policies.
- Adding or creating new custom policies.
- Editing or modifying existing policies.
- Removing policies as needed.
That’s it! I hope this blog has helped you understand how to manage external access in Microsoft Teams. To further enhance security, you can verify external users with email OTP for better access management. If you have any questions, feel free to share them in the comments section below.







