Disable Microsoft Exchange Unnoticed Basic Authentication Protocols in One Go!
Previously, on October 1, 2022, Microsoft stated that it would begin to disable basic authentication for Exchange Online. As of November 2022, Microsoft has deprecated basic authentication protocols for all Office 365 organizations unless they have requested a temporary pause.Despite efforts todeprecate Basic authenticationover several years, SMTP Auth remained an exception.But the exceptionis no more!Microsoftannouncedthe decisive step to remove Basic authentication entirely from Client Submissionon April 15, 2024.
But in reality, have all thebasic authentication protocols been disabled? Unfortunately, no! It’s true that turning off basic authentication in Microsoft 365 admin center does not disable all the legacy services.
Yes, Microsoft leaves some of the legacy services turned on, even if you turned off basic authentication protocols via Microsoft 365 admin center. Surprising, isn’t it? Yes, for real! So, with that said, let’s dive deep into the legacy auth protocols left uncared for and how to deal with them in this blog.
Every Office 365 tenant created after 2019 will have security defaults enabled (modern authentication) by default. If you wish to verify this, follow the path below and check whether the following image is obtained.
Microsoft 365 Admin Center → Settings → Org Settings → Modern Authentication (Under the ‘Services’ tab).
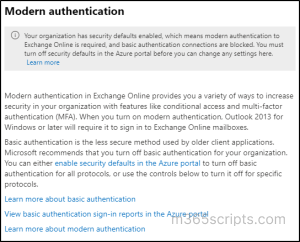
No worries if the above context is displayed! Your organization does not use basic authentication protocols. But what if it shows like the below image?
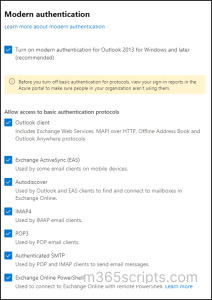
I see a lot of risks! Because, here, the organization still allows basic authentication protocols for their Office 365 users. So, it’s imperative to undergo the pivotal step of using the basic authentication report to identify users who are still using basic authentication methods.
Next, we will now disable the basic authentication protocols in use.
👆A click is all it takes to block basic authentication, and you’re done! Navigate to the below path and uncheck all the legacy services such as Outlook client, Exchange ActiveSync (EAS), Autodiscover, IMAP4, POP3, Authenticated SMTP, and Exchange Online PowerShell to block access to basic auth protocols.
Microsoft 365 Admin Center → Settings → Org Settings → Modern Authentication (Under the ‘Services’ tab).
By default, for newly created users, Exchange uses the tenant’s default protocol authentication policy. The Get-AuthenticationPolicy method will return a null value unless you define a default authentication policy in the organization.
However, when you change the basic auth access setting in the admin center, a default authentication policy will be created and registered in the organization policy. Since I have updated the basic authentication policy in the past, the default authentication policy got updated.
Below is an image of the updated authentication policy when I performed certain activities in basic auth protocols. To get the default authentication policy name, you can use the following cmdlet:
Get-AuthenticationPolicy | Format-Table –Auto Name
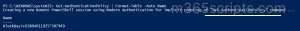
When the day came to turn off the legacy services, I blocked all the basic authentication protocols in Microsoft 365 admin center. But, eventually came to know that it didn’t surely block all the basic authentication protocols⚠️.
You can use the following command that details the authentication policies used in your organization and the status of each authentication protocol.
Get-AuthenticationPolicy
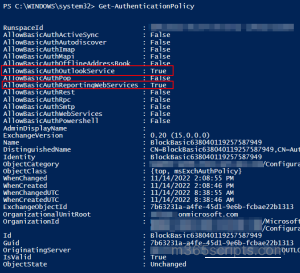
Finally, here is the final checkmate! And, now when you notice the above image, you will find the AllowBasicAuthOutlookService and AllowBasicAuthReportingWebServices are not completely disabled and their status is set to ‘True’ (i.e., They’re still currently in use).
These legacy services are used for the following purpose.
- AllowBasicAuthOutlookService – Specifies whether to allow basic authentication for Outlook services such as mail, and calendar apps.
- AllowBasicAuthReportingWebServices – Specifies whether to allow basic authentication with reporting web services to retrieve report data in Exchange Online.
But why does it really happen? Microsoft left turned on some reporting web services turned on to get access to Message tracking logs and more. Therefore, these reporting web services will be enabled until December 31st. Importantly, there is no opt-out or re-enablement required. However, if you do not want this basic authentication protocol to be turned on, Microsoft has provided a cmdlet solution.
Despite Microsoft didn’t block some basic authentication protocols and raising a big risk, there is an easy fix! All it takes is a single PowerShell cmdlet to block the left legacy auth protocols.
Set-AuthenticationPolicy -Identity " BlockBasic638040894239540475" -AllowBasicAuthReportingWebServices:$false -AllowBasicAuthOutlookService:$false

With the above image, now you can see AllowBasicAuthOutlookService and AllowBasicAuthReportingWebServices are set to false (i.e., allbasic authentication protocols are disabled completely).
Still not done! The previous command gets implemented only on new mailboxes any new mailboxes but not existing mailboxes. So, to apply the policy to existing mailboxes, use the following command:
$mbx = Get-Mailbox -RecipientTypeDetails UserMailbox -ResultSize unlimited
$mbx | foreach {Set-User -Identity $_.ExchangeObjectID.tostring() -AuthenticationPolicy <AuthenticationPolicyName>}
That’s it, there you go! Finally, we’ve blocked all the entry points for an attacker to enter our Office 365 organization. This blog hopefully sheds light on one of the riskiest and unnoticed legacy service allowances. Feel free to shoot your questions, we would be glad to assist you!
Startingin 2023, even re-enabled basic authentication protocols will be entirely disabled for Microsoft 365 organizations. So, whatever you do, never just stop at disabling—instead, start monitoring user sign-ins using basic authentication protocols.
But when it comes to reporting, Microsoft Azure’s basic authentication report falls short and is limited in scope, failing to deliver crucial insights like risk detection types, levels, etc.
So, for a more elaborate overview of basic auth protocol usage & every other Microsoft 365 service, move your cursor to AdminDroid Microsoft 365 reporter.
Wondering Why AdminDroid is a Top Choice for Exchange Online Management?
- Export anywhere, in any format! – You can export every Exchange Online report in various formats such as CSV, HTML, and PDF with just a click to analyze with greater flexibility.
- Schedule and sit back – Effortlessly set up automated schedules for daily monitoring reports like mailbox usage, spam & malware detections and receive real-time reports straight to your inbox. You won’t have to check reports manually anymore!
- Refine data intelligently – Now, you can merge multiple reports and apply additional filters, sorting, and columns for more effective mailbox traffic analysis.
- Delegate and share the load –Delegate access to reports, dashboards, tenants, etc., and work collaboratively. So that multiple team members can share the load of managing your Exchange Online environment.
- Don’t just crunch data in tables; visualize in charts! Visualize reports beyond the numbers & tables with our graphical AI charts. (Geo-map and heat map visualization). This makes it easier than ever to identify mailbox usage patterns and trends within an organization.
- Tenant management made easy – Manage multiple M365 tenants and get a bird’s eye view of everything in a single portal.
Moreover, the AdminDroid Exchange Online auditing tool comes packed with a whopping 170+ Exchange Online reports to track, schedule, and receive alerts on every criticalactivity. And as a cherry on top, admins can easily configure alerts and receive notifications whenever a user signs in using basic authentication with AdminDroid alerts. And the work is just a doddle; you won’t have to ponder anywhere!
Experience the full potential of the AdminDroid Exchange Online management tool now.
Preview the power of AdminDroid with a 15-day free trial now!