Identify the Conditional Access Policy Blocking a User Sign-in
Identify Conditional Access policies blocking user sign-ins by reviewing Microsoft Entra sign-in logs. Analyze error code 53003 BlockedByConditionalAccess failures, determine which policy conditions caused the block, and resolve access issues by adjusting policy configurations or user assignments.
In Microsoft Entra ID, Conditional Access policies are essential for enhancing security by controlling how users access cloud apps based on specific conditions. While these policies are powerful, they can sometimes lead to sign-in failures in Microsoft 365, leaving users and admins puzzled. When a user’s access is unexpectedly blocked, it can be frustrating and disruptive. Admins need to identify the issue quickly to restore the user’s access and prevent further inconvenience. In this blog, let’s walk you through the Conditional Access policy blocking a user’s sign-in, with detailed steps.
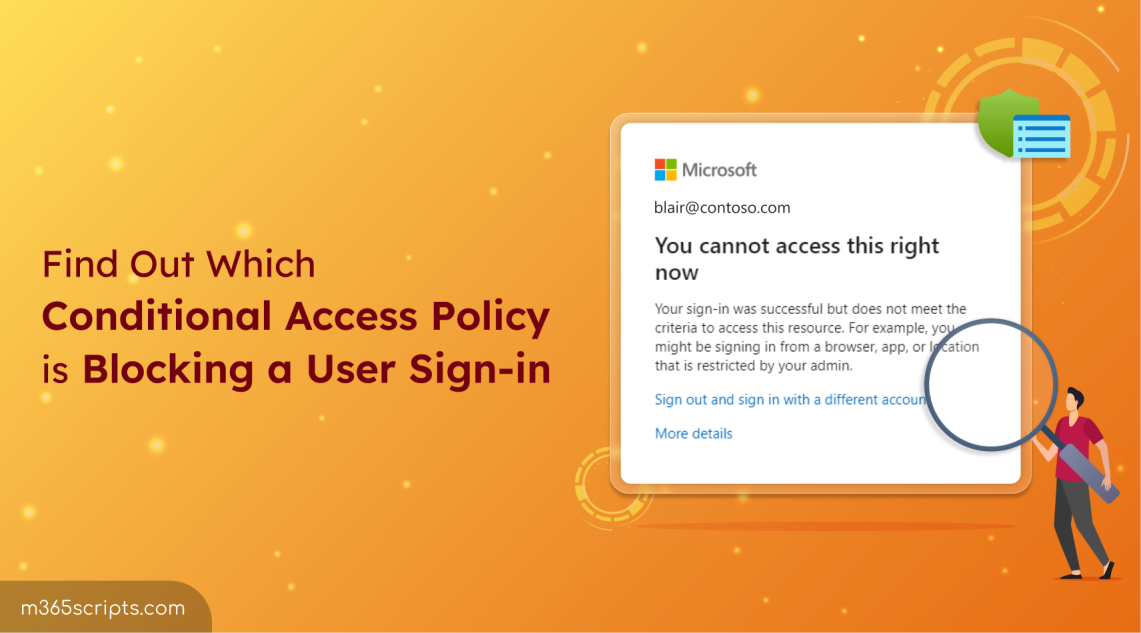
When Conditional Access policy impacts on user sign-ins, they might encounter a ‘You cannot access this right now’ error message like:
“Your sign-in was successful but does not meet the criteria to access this resource. For example, you might be signing in from a browser, app, or location that is restricted by your admin.”
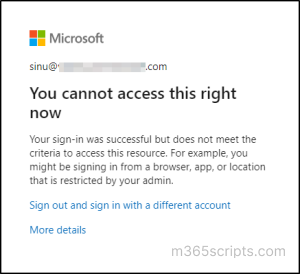
The associated sign in error code 53003 is usually due to “BlockedByConditionalAccess” error. This message means that even though the user’s credentials were correct, their sign-in access has been blocked by the Conditional Access policies.
Tracking sign-in logs in Microsoft Entra ID is the efficient way to check which Conditional Access policy is blocking the user’s login.
To access sign-in report in Microsoft Entra ID, you need either a Reports Reader, Security Reader, Security Administrator, Global Administrator, or Global Reader role.
The sign-in activity report in the Entra admin center is available in all the editions of MS Entra ID. However, you’ll require an Entra ID P1 or P2 license if you wish to access the report through Microsoft Graph API.
To pinpoint the exact Conditional Access Policy causing the issue, follow these steps:
- Sign in to the Microsoft Entra admin center.
- Navigate to Identity –> Monitoring & health –> Sign-in logs.
- Use filters like username, application, status, or other relevant fields to get the failed sign-in attempts in Microsoft 365.
- Click on the specific failed sign-in attempt and select the Conditional Access tab.
- Review the policies listed. The ones showing a “Failure” status with Grant Controls set to “Block” are the policies preventing the user from signing in.
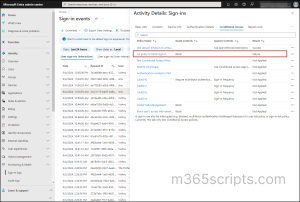
You can also access Conditional Access sign-in logs in Entra ID, by navigating through Identity –> Protection –> Conditional Access –> Sign-in logs in Entra admin center.
By following these steps, you can quickly identify which Conditional Access policy is blocking a user’s log-in attempt.
Alternative Ways to Find Out Check Which Conditional Access Policy Blocks User Sign-in
- You can use Sign-in Diagnostics in Microsoft Entra to identify which Conditional Access policy is blocking a user’s sign-in. This helps you understand why the policy was triggered and make necessary adjustments.
- Alternatively, Log Analytics in Microsoft Entra ID allows for more in-depth analysis. By querying sign-in logs using Kusto Query Language (KQL), you can identify patterns and Conditional Access policies associated with failed sign-ins.
Important Tips to Troubleshoot
- To troubleshoot sign-in issues with CA policy, use the Conditional Access What If tool. This tool helps validate policies before applying them broadly, reducing unexpected issues.
- To assess the impact of Conditional Access policies in your organization, use the Conditional Access insights and reporting workbook provided in Entra ID. This workbook provides detailed insights, helping you identify why users may have failed to comply with CA policies.
- If a Conditional Access policy uses an IP range based named location that is not trusted, sign-ins from that location will be blocked. Make sure trusted locations are correctly configured to prevent users from being denied access.
- If you happen to delete a Conditional Access policy while troubleshooting, Entra ID keeps deleted policies for 30 days. You can easily restore deleted CA policy from Conditional Access > Deleted Policies (Preview).
I hope this blog guided you through how to identify the CA policy that is blocking a user’s sign-in. Feel free to reach us through the comments section if you have any queries.







