Find MFA Setting Status Using Authentication Methods Policy Report in MS Entra ID
Since the user MFA registration details reports were out, it’s been a huge helpful in various ways! But, there has been a huge request on getting much closer to the MFA authentication methods. And, now this time, Microsoft not only heard but delivered – introducing the ‘Authentication methods policy report’ in Entra ID. The existing Authentication methods page helps to identify only the MFA user registration details, but this new preview feature allows admins to delve into per-user MFA settings and status.
This granular approach empowers admins to pinpoint and address weak security settings, ultimately enhancing the overall MFA configuration for their users.
Wondering how to maximize the MFA strengths for individual users using this feature? Let’s dive in.
This report offers a holistic view of a user’s MFA configuration, ensuring that no authentication method is overlooked! Administrators can quickly identify which MFA methods are enabled or disabled for each user, ensuring thorough coverage of security measures. Using the Authentication methods policy report of a single user offers several benefits for administrators and users, including:
- Granular User Control: This report enables Microsoft 365 admins to finely adjust MFA settings for each user. It offers insights into the status of each MFA method, enabling admins to customize authentication settings to suit individual user needs and risk profiles.
- Identify and remediate weak authentication settings: Admins can quickly spot which authentication methods are enabled for each user and identify any vulnerabilities. For instance, if a user has MFA enabled but relies solely on SMS as a second factor, administrators can prompt them to adopt more secure options like an Authenticator app.
Microsoft 365 admins have the below two methods to monitor authentication methods for each user. While the first method offers basic insights, the second provides granular MFA settings, which is the new preview feature.
- Get Azure AD user authentication methods in Entra ID
- Retrieve user’s MFA setting status with authentication methods policy report
The first existing way to find a user’s MFA method is by accessing the user’s authentication methods page. With this report, admins can identify the MFA methods a user has registered with their accounts. Furthermore, this assists admins inensuring that users utilize robust authentication methods.
To find the multi-factor authentication methods activity report for a specific user in Entra ID, follow these steps:
- In the Microsoft Entra admin center, navigate to the ‘Identity’ tab.
- Click onthe ‘Users’ tab and then select the ‘All users’ option.
- Choose the user you wish to check the authentication methods for.
- Select the ‘Authentication methods’ tab under the ‘Manage’ section.
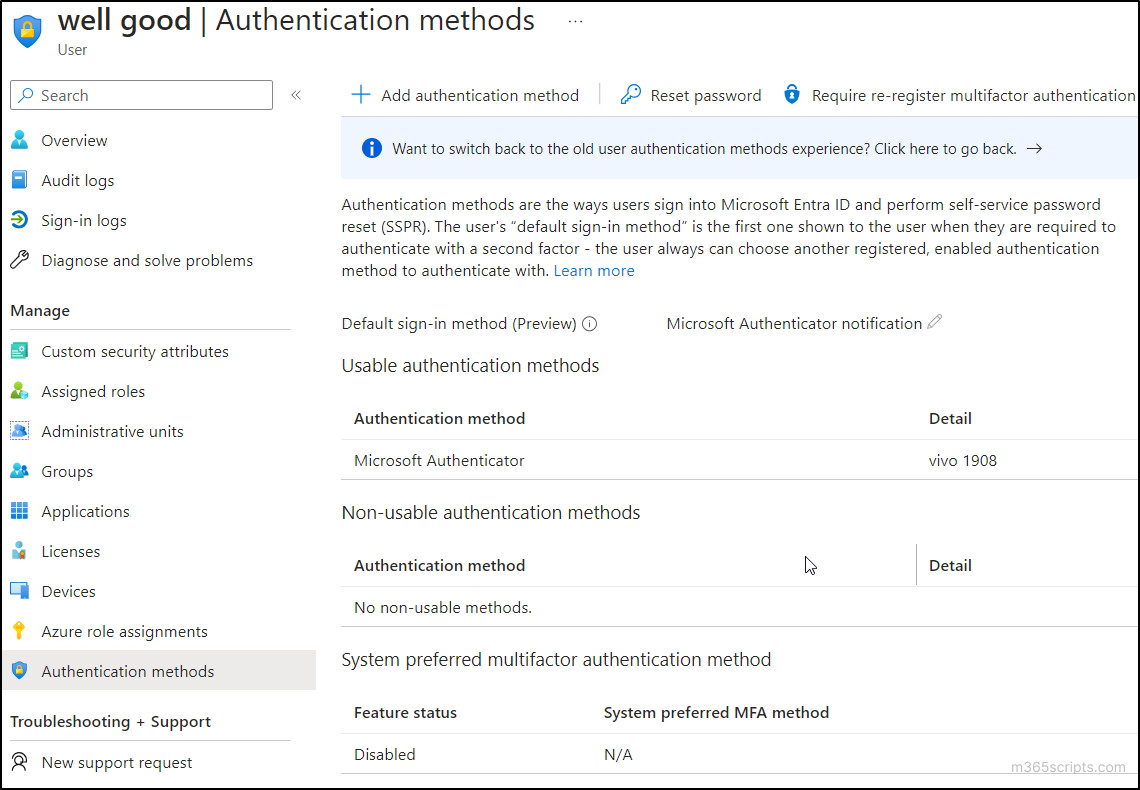
- Here, you can find the ‘user authentication methods information’. This page provides the following details about the user’s authentication methods.
-
- Default sign-in method:This shows the authentication method that a user has set as their default one. Previously, only users could modify the default MFA method, but now admins can change the default MFA method for M365 users.
- Usable authentication methods: Usable authentication methods are the enabled and currently active MFAs available for the use ofthe corresponding user.
- Non-usable authentication methods: These are the MFAs temporarily disabled for various reasons.
- System-preferred MFA method: Regardless of the default MFA method, the system-preferred MFA is the most secure method among those registered for the user, determined by Microsoft.
Previously, the above procedure is the only way to check whether the required MFA method was enabled or disabled for a user. But now, Microsoft has introduced a significant enhancement, which is way more granular than the existing one! Yes, you can now view the per-user-specific MFA settings status under each authentication method.
For example, you can check the attestation enforced state and self-service registration state for the FIDO2 security key authentication method.
This report is incredibly helpful, right? To access the MFA settings for each authentication method, follow these steps:
- Navigate to the ‘Identity’ tab in the Microsoft Entra admin center.
- Click onthe ‘Users’ tab and then select the ‘All users’ option.
- Choose the user you wish to check the Authentication methods policy report.
- Select the ‘Authentication Methods’ tab under the ‘Manage’ section.
- Click on ‘View authentication methods policy’ in the header of the page; this action will redirect you to a new page.
Note: If you can’t find this option, click on the three dots (…) and select ‘View authentication methods policy’ from the dropdown menu.
- Once redirected, the ‘Authentication methods policy (Preview)‘ page will appear!
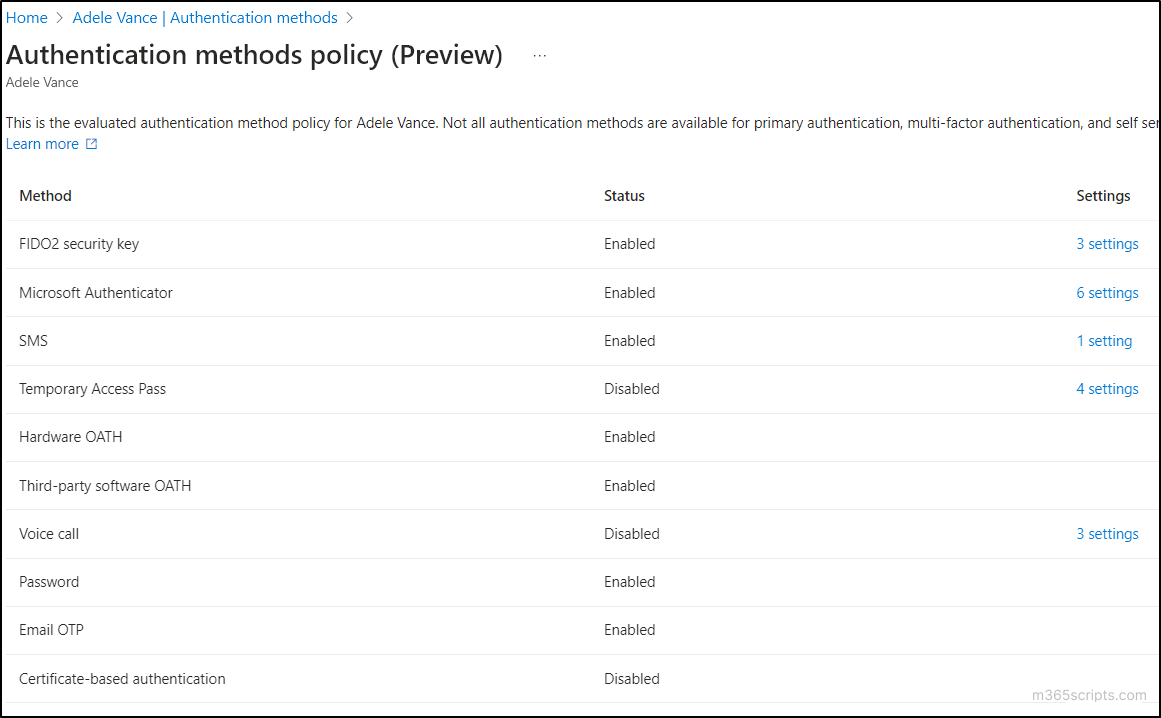
- This page will display all the MFA status in Microsoft 365.
- It also indicates whether each method is enabled or disabled and displays their specific configurations.
- Now, to view the settings associated with a specific authentication method, simply click the ‘number count’ in the ‘Settings’ column and view the MFA setting status for the user.
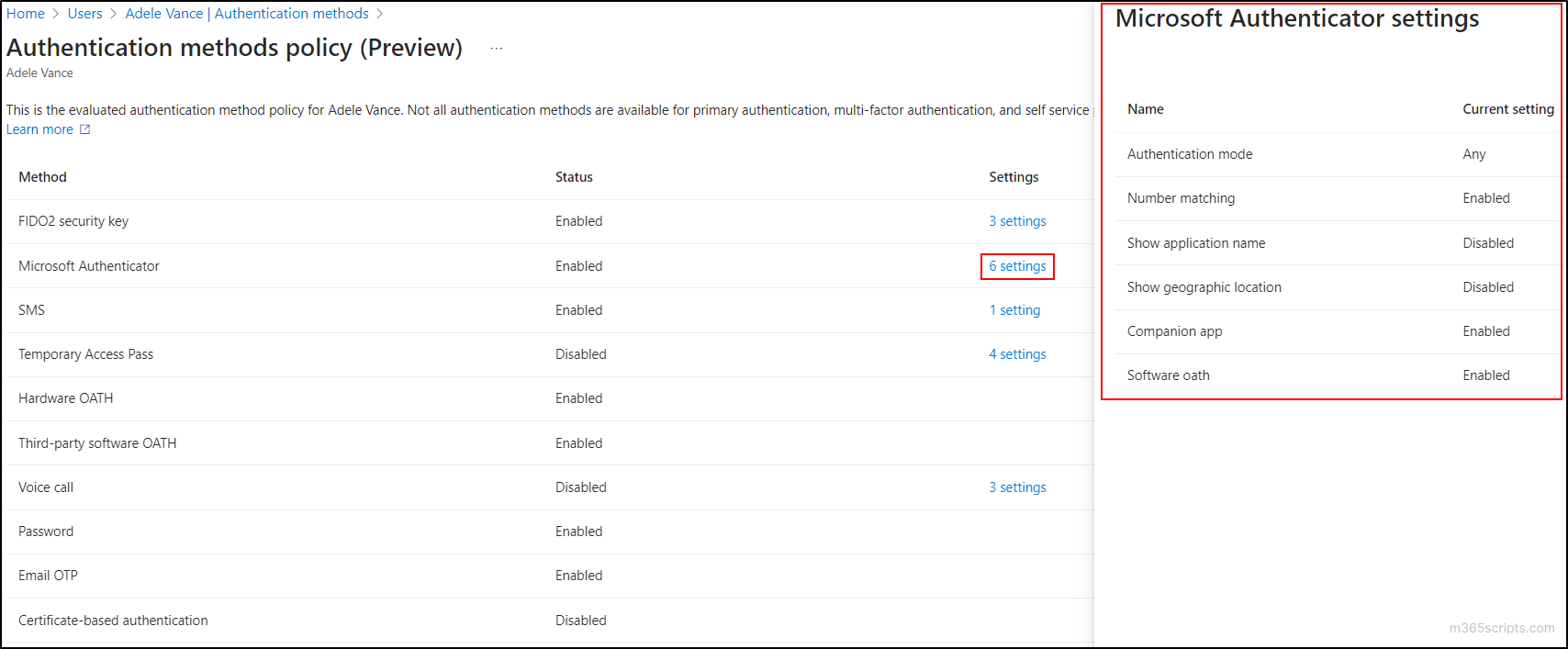
After analyzing the settings, administrators can become aware of the configurations applied to a specific user for the respective MFA authentication methods. This enables administrators to configure additional settings for the user in the appropriate authentication method to enhance security.
Here are a few examples that easily illustrate the importance of the Authentication methods policy report of a user:
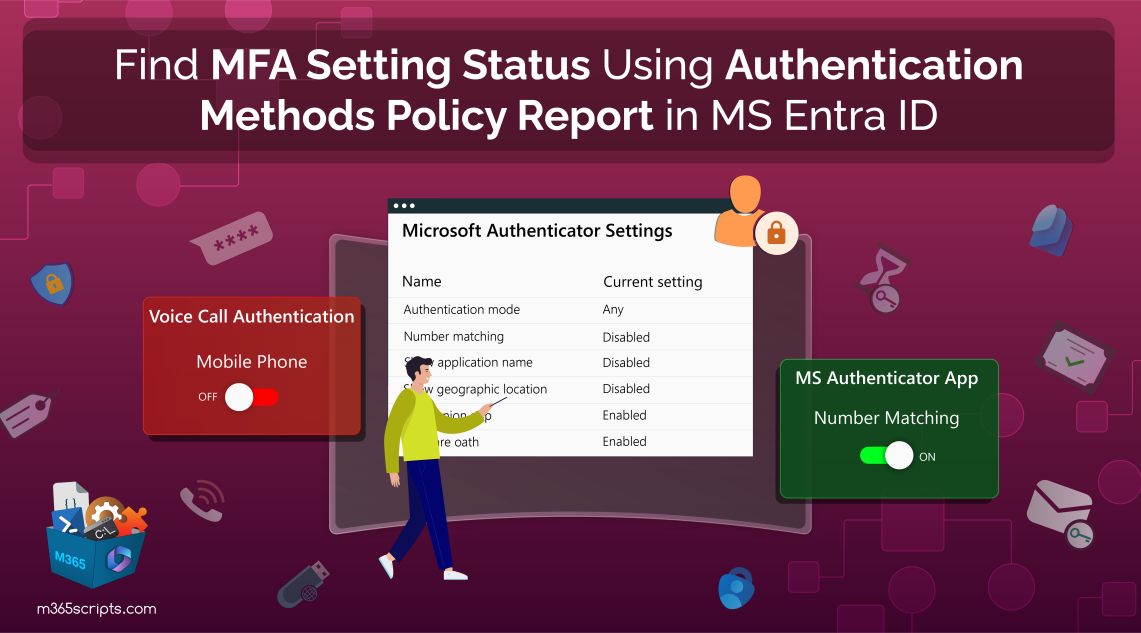
Example 1: Imagine a scenario where a user with Microsoft Authenticator has ‘Number matching’ disabled. In this case, MFA fatigue attacks via push notifications can potentially make the user vulnerable to attackers if they accidentally press ‘Accept’.
- Here, this report efficiently helps the M365 admins to examine such users and enable MFA number matching for those users immediately!
Example 2: When using Voice call authentication, it’s advisable to enable ‘Office Phones’ rather than ‘Mobile Phones’ to prevent potential misuse. This is due to the increased security risks associated with unmanaged devices on insecure networks. Identifying these less secure configurations helps administrators strengthen security.
In the scenarios described above, the report empowers administrators to enhance security by enabling advanced and high-impact authentication settings. This, in turn, provides an additional layer of protection for users, ultimately ensuring safer and more secure sign-ins.
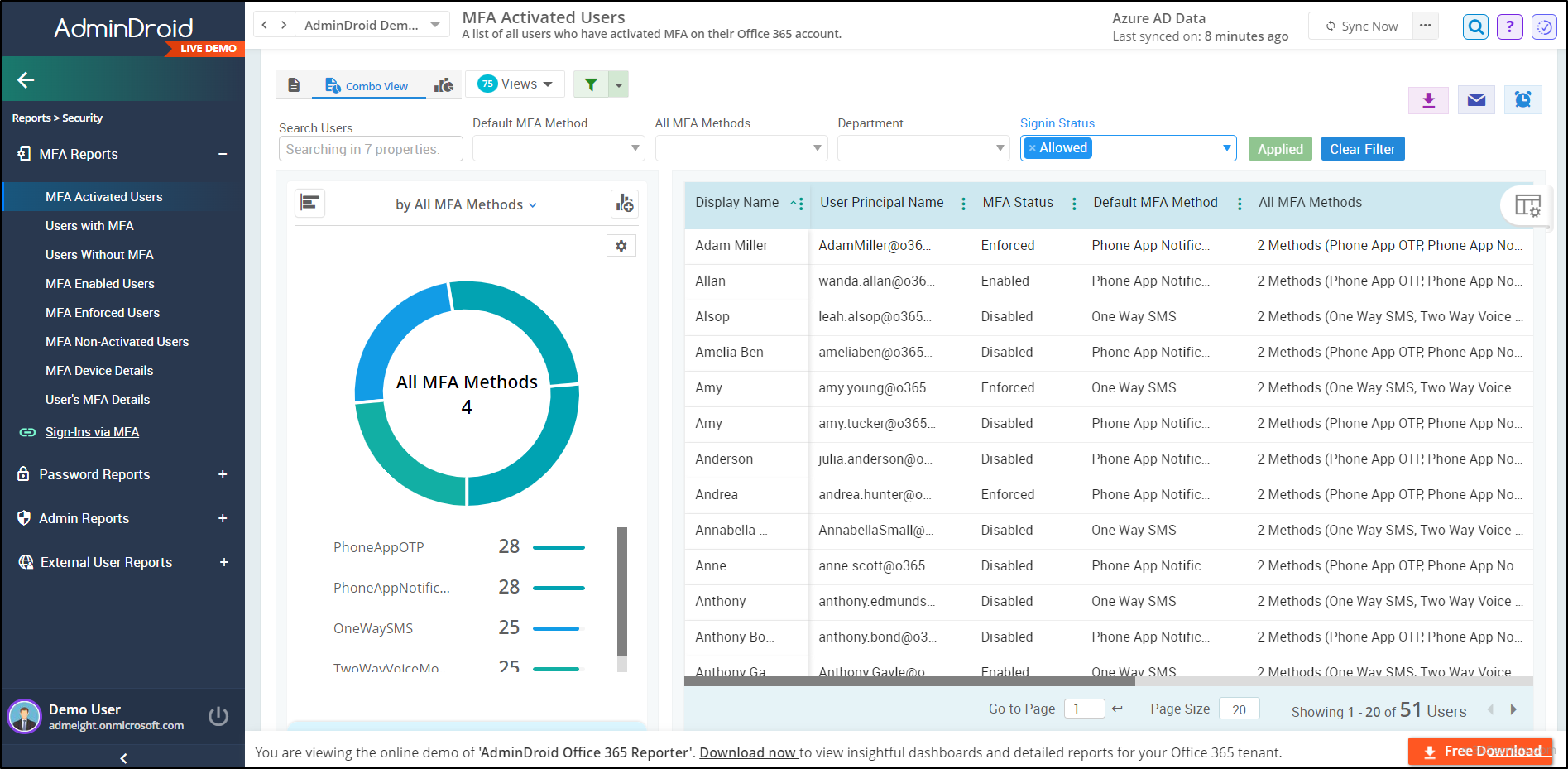
Struggling to find vital MFA statistics for all M365 users within the Entra admin center? This search, especially for reports on successful/failed MFA sign-ins and failure reasons, can be frustratingly time-consuming 😫. Bid farewell to those hassles and stop jumping around! The cool solution is here – AdminDroid, your Microsoft 365 reporting powerhouse.
AdminDroid MFA reports deliver configuredMFA methods, default MFA, MFA activation status, and user sign-in state for all users in a single, all-in-one pane with just a single click!
| Report | Using Entra ID | Using AdminDroid |
| MFA methods registered for a user | Authentication methods-user registration details page | MFA Activated Users Report |
| Default MFA method of a user | ||
| MFA status of a user | Per-User MFA page | |
| Sign-in state of a user | Entra ID user’s property page |
In addition to MFA insights, the security report collection encompasses user password reports, admin reports, and external user reports within the AdminDroid Azure AD reports branch.
AdminDroid’s Azure AD auditing tooloffers real-time insights into user logins, groups, app usage, and vital changes such as password resets and more. What’s more, both Azure AD reporting and auditing are entirely free, making it a valuable, cost-effective solution!
AdminDroid goes beyond Azure AD management (Entra ID) and extends its capabilities to all Microsoft services. This includes MS Teams, Exchange Online, SharePoint Online, Viva Engage, Stream, Power BI, OneNote and more.
✅ Lifetime free access to 120+ Azure AD (Entra ID) reports.
✅ Effortless Microsoft alerting, compliance auditing, and delegation to reporting.
✅ 30+ powerful dashboards and a total of 1800+ reports.
✅ AI-powered graphics charts with advanced customization.
✅ FREE premium edition for 15 days.
Download AdminDroid today and monitor your Microsoft 365 tenant like a pro 😎.
Final Thoughts!
Overall, the Authentication methods policy report in Entra ID is a boon for M365 admins who want to take their MFA security to the next level. With its granular insights, admins can easily identify and address weak security settings, ensuring that every user is protected with the strongest possible MFA configuration. This helps protect your users from even the most sophisticated attacks, leading to a more secure organization overall. Please feel free to leave yourcomments if you have any questions or need assistance.
Your Security, Your Way: Monitor User Authentication with Entra ID!